Table Of Contents
Feeling that familiar pang of frustration when your critical systems just won't talk to each other? You're not alone, especially when it comes to the intricate world of connecting remote IoT devices to AWS VPC. It's a situation many face, a bit like trying to open a secure file link that keeps saying "cannot connect," or finding your usual trusted site suddenly stops working. When you're trying to get your IoT setup to work, and you see that message – "securely connect remoteiot vpc aws not working" – it can feel like a real puzzle.
This challenge is quite common, you know, and it often feels similar to those moments when you're trying to send a confidential document securely, perhaps through SharePoint or Outlook, and it just doesn't seem to go through as expected. The desire to keep things safe, to ensure your sensitive data or device communications are protected, is a big deal. Yet, when the connection fails, it leaves you wondering what went wrong. It's a bit like an update that keeps trying to reinstall and fails, or when you can't log in because of a certificate issue; the core problem is a broken trust or a misconfigured pathway.
So, if you've been pulling your hair out trying to figure out why your remote IoT devices aren't making a safe connection to your AWS Virtual Private Cloud, you've landed in the right spot. We're going to look at the common snags that pop up when you're trying to get things to work, especially when you're aiming for a strong, safe link. This article will help you understand the usual suspects behind the message "securely connect remoteiot vpc aws not working" and give you some pointers on how to get your system talking again, you know, with all the necessary protections in place.
- Denzel Washington Training Day
- Paleseafoam Leaks Of
- Horses Mating
- Riley Green Political Party
- Aishah Sofey Only Leak
- The Challenge of Secure IoT Connections to AWS VPC
- Common Reasons Securely Connect RemoteIoT VPC AWS Not Working
- Steps to Diagnose and Fix Your Connection Woes
- Best Practices for Future-Proofing Your Secure IoT Connectivity
- Frequently Asked Questions
The Challenge of Secure IoT Connections to AWS VPC
Connecting anything over a network can present its own set of puzzles, and when you add the need for a strong, safe link, things get even more interesting. For those working with remote IoT devices and AWS, making sure these devices can talk to services within a Virtual Private Cloud (VPC) without exposing them to the wider internet is a big goal. It's about keeping your data and operations private, which is, you know, very important. When you see the phrase "securely connect remoteiot vpc aws not working," it points to a problem in this delicate balance of access and protection.
Why Connections Go Awry
You know, it's a lot like when you're trying to use a site that suddenly gives you a "cannot connect securely to this page" message. There are so many moving parts that have to line up just right for a connection to happen. With IoT devices, you have the device itself, its software, the network it's on, and then all the pieces of your cloud setup. If any one of these parts isn't quite right, the whole thing can fall apart. It could be something as simple as a forgotten setting or a more involved issue with how different security layers are interacting, or rather, not interacting. Just like a secure file upload link for financial documents might fail if the permissions are off, your IoT connection needs every piece of its security chain to be perfectly aligned.
Sometimes, the issue stems from a misunderstanding of how the various components are meant to interact. You might think you've set up everything correctly, but there's a small detail, a tiny configuration, that's preventing the handshake. This is a common experience, like when you're trying to figure out why a Windows 11 site suddenly stopped working, or why an update keeps trying to reinstall and fails. The problem isn't always obvious, and it can hide in plain sight, you know. When it comes to "securely connect remoteiot vpc aws not working," the root cause often lies in a mismatch between what the device expects and what the cloud service is providing, or vice versa, in terms of security credentials or network pathways.
- Lamar Jackson Injury History
- Emily Campagno
- Bomb Threat At Atlanta Airport Today
- Iran Economy 2024
- Exploring Malachi Bartons Relationships The Young Stars Personal Connections
The Role of VPC Endpoints and PrivateLink
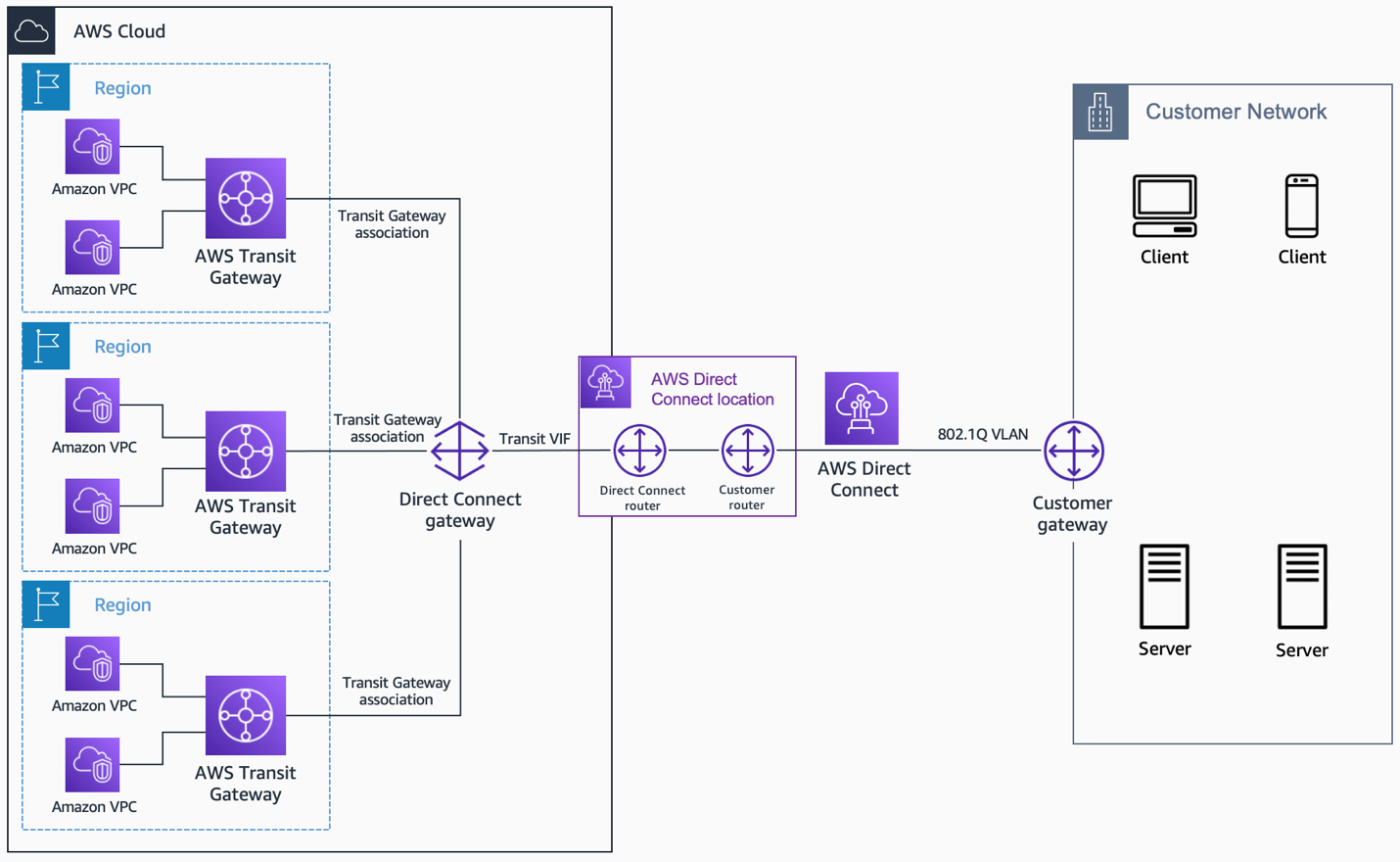
To keep IoT device traffic within your private network, you often use AWS VPC Endpoints and AWS PrivateLink. These services let your devices, even those out in the field, talk to AWS services like IoT Core without their data ever going over the public internet. This is a big deal for keeping things safe, as a matter of fact. A VPC endpoint acts like a direct, private connection to a service within AWS, from your VPC. It's like having a dedicated, private road straight to your destination, instead of taking the public highway.
PrivateLink, on the other hand, is the underlying technology that powers these endpoints. It helps you expose your own services, or consume AWS services, privately within your VPC. So, when your IoT device tries to connect to AWS IoT Core, it's often trying to reach an IoT Core VPC endpoint. If this private pathway isn't set up just right, or if there's a blockage along the way, that's when you'll hit the "securely connect remoteiot vpc aws not working" wall. It's a fundamental part of the secure connection, and any hiccup here can stop everything cold, you know.
Common Reasons Securely Connect RemoteIoT VPC AWS Not Working
There are several usual suspects when you find your remote IoT device connection to AWS VPC isn't working as it should. It's a bit like troubleshooting why you can't share a SharePoint link securely with an external user; you have to check multiple layers of access and permissions. Identifying the exact cause means looking at each part of the connection chain, one by one. This approach can save you a lot of time and frustration, you know, by narrowing down the possibilities.
Certificate and Policy Mismatches
One of the most frequent reasons for a connection failure, especially when you're trying to "securely connect remoteiot vpc aws not working," comes down to certificates and policies. Think of it like trying to log in and getting a message that you "can’t connect securely to this page" because the site uses "outdated or unsafe TLS security." Your IoT device needs a digital certificate to prove its identity to AWS IoT Core, and IoT Core needs to recognize that certificate. If the device's certificate is wrong, expired, or not registered correctly with IoT Core, the connection will simply not happen.
Then there are the IoT Core policies. These policies are like a set of rules that tell AWS IoT Core what a specific device is allowed to do. Can it publish messages? Can it subscribe to topics? Can it connect at all? If the policy attached to your device's certificate doesn't grant the necessary permissions to connect to the IoT Core endpoint, or to interact with the specific VPC endpoint, the connection will be denied. It's a fundamental security check, and if it fails, nothing else really matters, you know. You might have the right certificate, but the policy doesn't give it permission to use the private link.
This situation is quite similar to how you confirm in Outlook that an email was sent securely. You expect a certain confirmation, a sign that the security measures are in place and working. If that confirmation isn't there, or if the underlying security handshake fails, the communication doesn't happen. For IoT, the handshake involves the certificate and the policy. If either is off, the device won't be able to establish a safe pathway to your VPC, and you'll see that "securely connect remoteiot vpc aws not working" message pop up.
Network Configuration Headaches
Network settings are often a source of real headaches. We're talking about things like Security Groups, Network Access Control Lists (NACLs), and route tables within your VPC. These are the virtual firewalls and traffic directors that determine what can enter or leave your VPC, and where it can go. If your Security Groups don't allow inbound traffic on the correct port (usually 443 for MQTT over TLS) from your IoT devices, or if your NACLs are too restrictive, your connection attempts will just hit a wall, you know. It's like trying to get through a locked door that you forgot to unlock.
Also, the route tables in your VPC need to know how to direct traffic from your subnets to the VPC endpoint for IoT Core. If the routing isn't set up correctly, or if there's a more specific route overriding the one to your endpoint, the device's connection attempts will get lost. It's a bit like trying to send a large confidential file between two companies with Office 365, and the network paths aren't properly mapped for that kind of transfer. The data simply won't find its way. So, ensuring all your network components are allowing the right traffic in and out, and directing it correctly, is absolutely necessary for your device to connect securely.
DNS Resolution Problems
DNS, or Domain Name System, is like the phonebook of the internet, but it's just as important within your private cloud. When your IoT device tries to connect to the AWS IoT Core endpoint, it needs to translate the endpoint's hostname (like `data.iot.region.amazonaws.com`) into an IP address. If you're using a VPC endpoint, this translation needs to point to the private IP addresses of that endpoint, not the public ones. If your DNS resolution isn't set up to use the private DNS names provided by the VPC endpoint, your device will try to connect to the public endpoint, which might not be allowed or configured for your private setup. This is a common trap, you know.
You might have private DNS enabled for your VPC endpoint, but your devices or your network might not be configured to use the VPC's DNS resolvers. This means they're still looking up public IPs, leading to connection failures. It's a subtle but powerful reason why "securely connect remoteiot vpc aws not working" shows up. Ensuring your DNS setup correctly points to the private endpoint is a step that often gets overlooked, but it's quite important for a smooth, private connection.
IAM Permissions and Roles
Beyond the IoT Core policies, the Identity and Access Management (IAM) roles and permissions play a significant part, especially if you're using something like AWS IoT Greengrass or other services that interact with IoT Core on behalf of your devices. The IAM role assumed by your IoT service needs to have the right permissions to create or manage things within IoT Core, or to interact with the VPC endpoint service. If the IAM role lacks the necessary permissions, operations might fail, which can indirectly prevent device connections. It's like trying to access customer files on SharePoint without the right user permissions; the system simply says no.
For instance, if your IoT Greengrass core device needs to connect to AWS IoT Core via a VPC endpoint, the IAM role associated with that Greengrass core needs permissions to do so. If these permissions are too restrictive, or if there's a missing action, the connection attempt will not succeed. It's a layer of security that works in conjunction with your device policies, and both need to be aligned for a successful and safe connection. This is, you know, a very important part of the overall security posture.
Firmware and SDK Issues on the Device
Sometimes, the problem isn't with AWS at all, but with the IoT device itself. The device's firmware or the SDK (Software Development Kit) it's using to connect to AWS IoT Core might be outdated, have bugs, or be misconfigured. For example, the SDK might not be properly configured to use the VPC endpoint's specific DNS name, or it might not be handling the TLS handshake correctly. This is a bit like when your Windows 11 system suddenly can't connect to a site it used to, perhaps after a mid-June update; the software on your end might be the culprit. You know, sometimes the simplest explanation is the right one.
Ensuring that your device's software is up-to-date and that its connection parameters are exactly what AWS IoT Core expects for a VPC endpoint connection is quite important. This includes the endpoint URL, the port, and how it handles certificate validation. If the device's code isn't pointing to the correct private endpoint or isn't trusting the right certificate authority, it will fail to connect securely. It's a common oversight, and one that can lead to a lot of head-scratching when you're trying to figure out why "securely connect remoteiot vpc aws not working" keeps appearing.
VPC Endpoint Service Configuration
If you're creating your own VPC endpoint service for your IoT devices to connect to (perhaps to a service running in a different VPC), the configuration of that service itself is very important. This includes the service name, the network load balancer it points to, and the allowed principals. If the service name isn't correctly advertised, or if the network load balancer isn't healthy, devices won't be able to establish a connection. Furthermore, if the AWS account or IAM user trying to connect isn't listed as an allowed principal for the endpoint service, access will be denied. This is a rather specific but critical point of failure.
It's like trying to share sensitive documents between two companies; if one company hasn't properly set up its receiving end, or hasn't authorized the other company to send, the transfer won't happen. The VPC endpoint service needs to be correctly configured to accept connections from your specific devices or accounts. Any misstep here means the private pathway simply isn't open for business, leading to the familiar "securely connect remoteiot vpc aws not working" message. You know, every detail matters in these setups.
Steps to Diagnose and Fix Your Connection Woes
When you're facing the "securely connect remoteiot vpc aws not working" problem, a methodical approach to troubleshooting can save you a lot of time and frustration. It's about systematically checking each potential point of failure, much like when you're trying to figure out why a website you use suddenly stopped working on Windows 11. You start with the most common issues and work your way through the layers.
Verify Certificates and Keys
First things first, check your device certificates and private keys. Make sure the certificate on your IoT device is the correct one, that it hasn't expired, and that its corresponding private key is present and correctly configured on the device. Then, verify that this certificate is registered with AWS IoT Core and that it's active. You can do this in the AWS IoT Core console under "Security" and then "Certificates." It's a basic but absolutely essential step, you know, for any secure connection.
Also, ensure that the certificate authority (CA) certificate used by your device to verify the AWS IoT Core endpoint is the correct one and is up-to-date. If your device is trying to connect to a private VPC endpoint, it might need to trust a different set of CAs than it would for a public endpoint. This is a very common source of connection issues, as a matter of fact. A mismatch here is like trying to use an old, invalid ID card; the system just won't let you in.
Inspect IoT Core Policies
Next, carefully review the IoT Core policy attached to your device's certificate. Does it grant the necessary `iot:Connect` permission? Does it allow connection to the specific endpoint you're trying to reach? For VPC endpoints, the policy might need to include specific resource ARNs related to the endpoint. Make sure the policy allows the device to publish and subscribe to the topics it needs, and that the policy version is the one you intend to be active. Any missing permission here can stop the connection cold. This is, you know, a very common place for things to go wrong.
You can test the policy using the AWS IoT Core policy simulator to see if specific actions would be allowed or denied for your device. This tool can be incredibly helpful in pinpointing exactly which part of your policy is causing the problem. It's like double-checking the permissions on your SharePoint customer files before you try to send a secure link; you want to be sure everything is set up correctly before you even attempt the connection.
Review Network Paths
This is where you put on your network detective hat. Check your VPC Security Groups and NACLs. Ensure that inbound rules on the Security Group associated with your VPC endpoint allow traffic on port 443 (or your specific MQTT port) from the IP addresses or Security Groups where your IoT devices reside. Similarly, check outbound rules from your device's subnet to the VPC endpoint. Remember, NACLs are stateless, so you need both inbound and outbound rules for the same port. This is, you know, often a tricky part.
Look at your VPC route tables. Confirm that there's a route from the subnet where your VPC endpoint resides, or from the subnets your devices are in, to the target of your VPC endpoint. If you're using a VPC endpoint for IoT Core, the route should point to the endpoint ID. If traffic isn't routed correctly, it simply won't reach its destination. Tools like `traceroute` or `mtr` from a machine within your VPC (or a similar network debugging tool on your device, if possible) can help you trace the path and see where the connection might be getting blocked.
Check DNS Resolution
Verify that your IoT device is resolving the AWS IoT Core endpoint hostname to the private IP addresses of your VPC endpoint, not the public ones. From a machine within your VPC, or if possible, from the IoT device itself, use a DNS lookup tool like `dig` or `nslookup` on the IoT Core data endpoint hostname (e.g., `data.iot.us-east-1.amazonaws.com`). If it returns public IPs, your DNS setup is likely the issue. You need to ensure private DNS is enabled for your VPC endpoint and that your VPC's DNS resolvers are being used. This is, you know, a very common and often overlooked problem.
If your devices are outside the VPC and connecting via VPN or Direct Connect, ensure your on-premises DNS servers are configured to forward queries for AWS service endpoints to the VPC's DNS resolvers. This makes sure that the private IP addresses are returned. Without proper DNS resolution, your device will attempt to connect to the public endpoint, which, as a matter of fact, will likely fail if you've configured your IoT Core to only accept private connections.
Audit IAM Roles
If your setup involves AWS IoT Greengrass or other AWS services acting on behalf of your devices, check the IAM roles associated with those services. Ensure these roles have the necessary permissions to interact with AWS IoT Core and the VPC endpoint. This includes permissions like `ec2:DescribeVpcEndpoints` or `iot:Connect` for specific resources. A missing permission here can cause subtle failures that are hard to track down. It's like trying to securely erase a hard disk without the right administrative privileges; the action simply won't complete. This is, you know, a rather important step.
Test with AWS IoT Device Tester
- Denzel Washington Training Day
- Desmond Doss The Unyielding Spirit Of A Conscientious Objector
- Morten Harket The Voice Of Aha And His Enduring Legacy
- Riley Green Political Party
- Two Babies And One Fox
Securely Connect Remote IoT VPC AWS Not Working Windows: Comprehensive

Securely Connect Remote IoT VPC AWS Not Working Windows: A

Securely Connect Remote IoT VPC AWS Not Working Windows: A