Securely Connect Remote Iot Vpc
Securely Connect Remote IoT VPC: Your Essential Guide for Device Protection
Connecting devices from far away places to your central cloud network, what we often call a Virtual Private Cloud or VPC, is a big deal for many businesses these days. It's almost like setting up a secret, safe pathway for your smart gadgets to talk to your main hub. You see, with more and more things like smart sensors, cameras, and industrial machines sending information back and forth, making sure these connections are really safe is a top concern. Just as people need to send confidential papers without worry, these devices need to transmit their data without any trouble, too.
Think about it: whether it's a smart thermostat in a distant building or a fleet of delivery vehicles sending location updates, every piece of information needs to arrive safely and privately. If these connections aren't buttoned up, it could lead to all sorts of headaches, like someone snooping on your data or even taking control of your devices. This whole situation, you know, makes it super important to understand how to keep everything locked down.
- Exploring The Race Of Steve Perry A Deep Dive Into His Background And Legacy
- Riley Green Political Party
- Iran Live Cameras
- 2 Babies One Fox
- Aishah Sofey Onlyfans Leaked
This article will walk you through the key ideas and practical ways to securely connect remote IoT VPC setups. We'll talk about why it's so important, some common hurdles you might face, and the best ways to make sure your devices and data stay protected. It's about building trust in your system, very much like making sure a file you send to a client is truly private and only seen by the right eyes.
Table of Contents:
Why Secure IoT Connections Really Matter
Common Hurdles When Connecting Devices
Core Ideas for Keeping IoT VPC Connections Safe
Knowing Who or What is Connecting
Scrambling Your Information
Giving Just Enough Access
Watching What Happens
Ways to Securely Connect Remote IoT VPC
Private Tunnels (VPNs)
Direct Cloud Pathways
Secure Messaging Protocols
Smart Device Gateways and Edge Computing
Trust No One, Verify Everyone (Zero Trust)
Putting Security Layers in Place
Managing Who Can Do What
Keeping Network Parts Separate
Protecting Data Always
Checking Things Often and Staying Up-to-Date
Making Sure Connections Are Always Working
The People Part of IoT Safety
Frequently Asked Questions About Secure IoT VPC Connections
Why Secure IoT Connections Really Matter
In our modern world, where everything seems to be getting smarter, from our homes to big factories, the number of connected devices is just exploding. This growth, you know, brings amazing possibilities, but it also opens up new places where things could go wrong. Just like you'd want to be sure your sensitive financial documents are uploaded to a safe spot, companies need to make absolutely sure their IoT device connections are sound.
A big reason to care about security is data protection. IoT devices collect all sorts of information, some of it very personal or business-critical. If someone gets their hands on this data without permission, it could lead to privacy breaches, financial losses, or even harm to people. So, it's pretty clear that keeping this information private and secure is a very important job.
Then there's the risk of unauthorized access or control. An unprotected IoT device could be like an open door into your entire network. Someone with bad intentions might use it to mess with operations, steal secrets, or even launch attacks on other systems. This is why securing each connection point is a bit like locking every door and window in your house, just to be on the safe side.
Finally, there are rules and regulations. Many industries have strict guidelines about how data should be handled and protected. Not following these rules can lead to hefty fines and a damaged reputation. So, getting your IoT security right isn't just a good idea; it's often a requirement, you know, for doing business.
Common Hurdles When Connecting Devices
Even with the best intentions, securely connecting remote IoT VPC setups can present a few challenges. One common issue, apparently, is the sheer number and variety of devices. You might have old sensors working alongside brand-new smart gadgets, and getting them all to speak the same secure language can be a bit tricky. Each device might have its own quirks, too, making a one-size-fits-all security approach hard to achieve.
Another hurdle is network reliability. Sometimes, remote locations just don't have the best internet service. A shaky connection can cause data loss or, you know, make it impossible for devices to send their information securely. This is a bit like when you try to log into a website and get that "can't connect securely to this page" message, which is often because of outdated or unsafe security settings. For IoT, an unreliable connection means data might not get through, or it might be exposed if the secure tunnel drops.
Device vulnerabilities are also a concern. Many IoT devices are built for specific tasks and might not have strong security features right out of the box. They might use old software, have weak default passwords, or lack the processing power for complex encryption. Addressing these weaknesses, you see, requires careful planning and often some extra layers of protection.
Lastly, managing all this can be quite a task. Keeping track of every device, its security status, and all its connections can become overwhelming as your IoT setup grows. It's like trying to manage all your customer files in SharePoint; you need a good system to keep everything organized and secure, otherwise things can get messy pretty fast.
Core Ideas for Keeping IoT VPC Connections Safe
To really securely connect remote IoT VPC environments, there are some basic ideas that always help. These are the building blocks for a strong security plan, you know, for your devices and data.
Knowing Who or What is Connecting
First off, it's super important to know exactly who or what is trying to connect to your network. This is often called "authentication." It means making sure that only authorized devices and users can even try to send data or receive commands. This might involve unique digital identities for each device, special certificates, or even strong passwords that are never the default ones. Just like you need a certificate and a PIN to log in securely to some services, your devices need their own way to prove they are who they say they are. This helps stop unwanted guests from getting in, very much like making sure only the right person can access a secure file upload link.
Scrambling Your Information
Once you know who's connecting, the next step is to scramble all the information being sent. This is called "encryption." It turns your data into a secret code that only the intended receiver can unscramble. Even if someone manages to grab the data while it's traveling, they won't be able to read it. This is a bit like putting your confidential documents in a locked box before sending them; only the person with the key can open it. This protects your data both when it's moving and when it's sitting still, just waiting to be used.
Giving Just Enough Access
Another key idea is giving devices and users only the access they absolutely need to do their job, and no more. This is often referred to as "least privilege." For example, a temperature sensor only needs to send temperature readings; it doesn't need to control a factory machine. Limiting access like this reduces the damage that could be done if a device somehow gets compromised. It's like giving someone a key to just one room, not the whole building, you know, keeping things tidy and safe.
Watching What Happens
Finally, you need to keep a close eye on everything that's happening. This means constantly monitoring your connections and devices for any unusual activity. If a device suddenly starts sending huge amounts of data or tries to connect to strange places, that could be a sign of trouble. Having good monitoring tools helps you spot problems early and react quickly. It's like having security cameras watching your property; you want to know if anything seems out of place, so you can deal with it right away.
Ways to Securely Connect Remote IoT VPC
There are several tried and true methods to securely connect remote IoT VPC environments. Choosing the right one often depends on your specific needs, the types of devices you have, and where your cloud network is set up. All of these options aim to build that safe, private pathway for your IoT data.
Private Tunnels (VPNs)
One very common way to create a secure connection is by using Virtual Private Networks, or VPNs. A VPN basically creates a private, encrypted tunnel over the public internet. It's like having a secret road just for your data. You can set up "site-to-site" VPNs that connect your remote locations directly to your VPC, or "client VPNs" for individual devices. This means all the data traveling through that tunnel is scrambled and protected, making it very hard for anyone to snoop on it. This is a pretty solid choice for many setups, you know, providing a good layer of privacy.
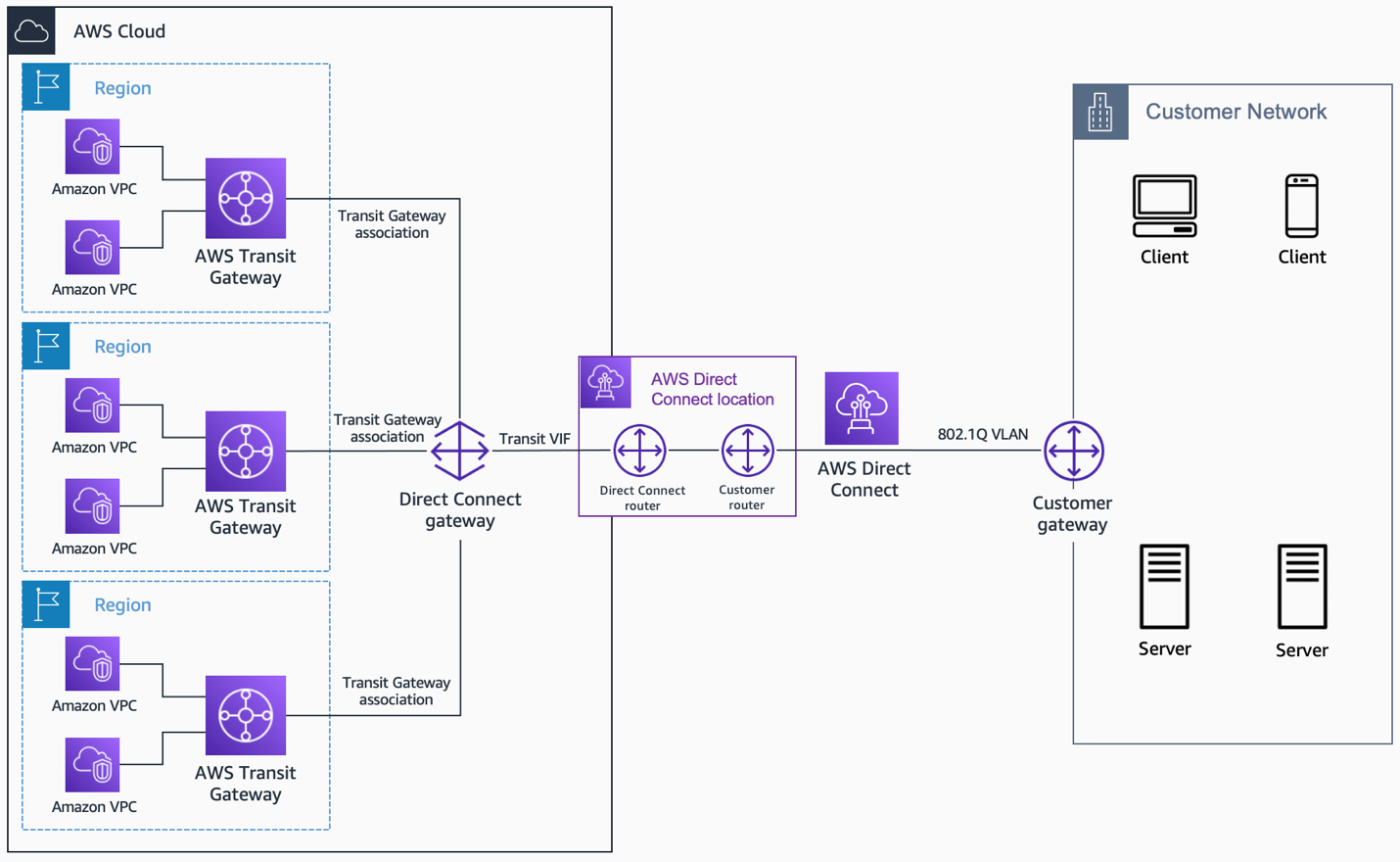
Direct Cloud Pathways
For even higher security and performance, especially if you're dealing with a lot of data or very sensitive information, you might consider direct cloud pathways. Services like AWS Direct Connect or Azure ExpressRoute create a dedicated, private network connection from your physical location straight to your cloud provider's network. This means your data never even touches the public internet, which makes it extremely secure. It's like having your own private highway directly to your cloud data center, rather than using the public roads. While it might be a bit more involved to set up, the peace of mind is often worth it, you know, for critical operations.
Secure Messaging Protocols
Beyond the network connection itself, the way your devices talk to each other also needs to be secure. Protocols like MQTT, which is very popular for IoT, can be secured using TLS/SSL encryption. This means that even if the underlying network isn't perfectly private, the messages themselves are scrambled. It's like putting individual letters in sealed, tamper-proof envelopes before sending them. This adds another layer of protection, making sure that the content of your messages stays private, even if the connection somehow gets intercepted. This is a fundamental part of keeping things safe, very much so.
Smart Device Gateways and Edge Computing
Sometimes, individual IoT devices aren't powerful enough to handle complex security tasks on their own. That's where device gateways and edge computing come in. A gateway is a central point at a remote location that collects data from many devices, processes it, and then sends it securely to the cloud. This gateway can handle the heavy lifting of encryption and authentication for all the devices connected to it. Edge computing takes this a step further, allowing some data processing and analysis to happen right there at the remote location, reducing the amount of data that needs to be sent to the cloud. This can make your overall system much more efficient and secure, you know, by keeping more data local.
Trust No One, Verify Everyone (Zero Trust)
A more advanced approach to security is the "Zero Trust" model. This idea, basically, means that you don't automatically trust anything or anyone, whether they are inside or outside your network. Every device, every user, and every connection has to be verified before it's allowed to do anything. This is different from traditional security, which often assumes things inside the network are safe. With Zero Trust, even if a device is already connected, it still needs to prove it should have access to specific resources. This makes it incredibly hard for attackers to move around your network, even if they manage to get a foot in the door, very much like a strict security checkpoint for every single action.
Putting Security Layers in Place
To truly securely connect remote IoT VPC setups, it's not enough to just pick one method. You really need to build multiple layers of protection, like an onion. Each layer adds a bit more safety, making it harder for anyone to break through. This layered approach helps cover all your bases, you know, for comprehensive protection.
Managing Who Can Do What
A big part of security is managing who has access to what. This is often called Identity and Access Management, or IAM. For IoT, this means creating unique identities for each device and user, and then setting very clear rules about what they are allowed to do. For instance, a temperature sensor might only have permission to send data to a specific cloud service, but not to change any settings. Regularly checking and updating these permissions is also very important. It's like having a very precise set of keys for every lock, making sure only the right key opens the right door.
Keeping Network Parts Separate
Another smart move is to keep different parts of your network separate. This is known as network segmentation. You can use things like subnets and security groups within your VPC to create isolated sections. For example, your IoT devices might be in one part of the network, while your main business applications are in another. If one part gets compromised, the damage is contained and doesn't spread to other critical areas. This is a bit like putting different types of documents in separate, locked cabinets; if one cabinet is breached, the others are still safe, you know, for added peace of mind.
Protecting Data Always
Data protection isn't just about scrambling information as it travels. It also means protecting it when it's sitting still, like in a cloud database or on a device's storage. This is called "encryption at rest." Using encryption for stored data means that even if someone manages to get a hold of your data files, they won't be able to read them without the right key. This provides a constant layer of protection, similar to how you'd want to securely erase a hard drive before recycling it, making sure no one can recover your old files. It's about ensuring your information is unreadable to unauthorized eyes, you know, at all times.
Checking Things Often and Staying Up-to-Date
Security isn't a one-time setup; it's an ongoing process. You need to regularly audit your security settings, check for any weaknesses, and make sure all your software and device firmware are up-to-date. Attackers are always finding new ways to exploit vulnerabilities, so staying current with patches and updates is really important. It's like maintaining your car; regular check-ups and oil changes keep it running smoothly and safely. Neglecting updates can leave you exposed, very much like how a site you use might suddenly stop working on Windows 11 if it relies on outdated security. Industry groups often provide guidelines for these sorts of things, too, which can be helpful.
Making Sure Connections Are Always Working
Beyond just being secure, your connections need to be reliable. It's pretty frustrating when you try to log in and get a "can't connect securely to this page" message, often because of outdated or unsafe security. For IoT, an unreliable connection means your devices might stop sending data, or worse, they might become unresponsive. This is why building in redundancy, having backup connection methods, and using robust network components are key. You want your IoT system to be like a well-oiled machine, always on and always talking, you know, without hiccups. Regularly monitoring connection health and having alerts for any drops can help you fix issues before they become big problems.
The People Part of IoT Safety
Even with the best technology, people play a big role in keeping things secure. Just as your business needs to send clients an email or a link for secure file upload for financial documents, the people managing your IoT system need to understand security best practices. This means training staff on how to handle sensitive data, recognize potential threats, and follow security procedures. It's about building a culture of security where everyone understands their part in keeping things safe. After all, a strong security system is only as strong as its weakest link, and often, that link can be human error. So, educating everyone involved is pretty much essential.
Frequently Asked Questions About Secure IoT VPC Connections
What are the biggest risks if my remote IoT VPC connection isn't secure?
If your remote IoT VPC connection isn't secure, you could face several big problems. Someone might steal your data, which could be private customer information or sensitive business details. Also, unauthorized people could take control of your devices, making them do things they shouldn't, or even use them to attack other parts of your network. This could lead to financial losses, damage to your reputation, and even legal issues, you know, if you're not careful.
How can I tell if my IoT device connections are actually secure?
You can confirm your IoT device connections are secure by regularly checking your network logs and security monitoring tools. Look for signs of unusual activity, failed connection attempts from unknown sources, or unauthorized data transfers. You should also make sure your devices are using strong encryption protocols like TLS/SSL and that their identities are being properly verified. It's a bit like trying to confirm in Outlook that the secure email you sent was indeed sent securely; you look for specific indicators and rely on the system's built-in checks, you know, to give you peace of mind.
What's the difference between VPNs and direct cloud pathways for IoT security?
VPNs (Virtual Private Networks) create an encrypted tunnel over the public internet, making your data private as it travels. They're a good, flexible option for many situations. Direct cloud pathways, on the other hand, create a dedicated, private connection straight from your physical location to your cloud provider's network, bypassing the public internet entirely. This often offers higher performance and even greater security because your data never touches the open web. The choice depends on your security needs, data volume, and budget, you know, for what works best.
Learn more about on our site, and link to this page .
- Leanne Morgan Journey Concert
- Agentredgirl
- Lifemd Reviews
- Fiona Gallagher Shameless
- Roma Downey Feet
Securely Connect Remote IoT VPC AWS Not Working Windows: Comprehensive

Securely Connect Remote IoT VPC Raspberry Pi: The Ultimate Guide

Securely Connect Remote IoT VPC Raspberry Pi Free Android: The Ultimate