Securely Connect Remote IoT To AWS VPC: Keeping Your Devices Safe
Connecting remote IoT devices to your AWS Virtual Private Cloud (VPC) isn't just a good idea; it's absolutely vital for keeping your operations running smoothly and, well, safely. You know, like when you're trying to send important financial documents, you want to be sure they get there without a hitch, and without anyone else peeking. It's that same feeling of needing a rock-solid, private connection, but for your smart devices out in the world. Just as we want to be sure our emails are sent securely, or that a website connection isn't using outdated security, your IoT data deserves that same careful attention.
Think about all the sensitive information your IoT devices might be gathering – maybe it's factory floor data, patient health readings, or even just temperature logs from a remote sensor. Letting that information travel across the open internet without proper safeguards is, quite frankly, a recipe for trouble. It's a bit like leaving your front door wide open when you're not home, isn't it? You want to make sure only authorized eyes see that data, and that it reaches its destination without being tampered with.
This article will show you how to build those strong, private connections between your remote IoT devices and your AWS VPC. We'll look at the tools AWS gives you, discuss some smart ways to set things up, and talk about why this kind of security really matters. So, if you're looking to make your IoT setup more resilient and private, you're in the right place. We're going to explore how to make those connections truly safe, actually.
- Benny Blanco Net Worth
- Post Nirvana
- Bomb Iran Vince Vance
- Unveiling The Charismatic Actor From Mad Men A Journey Through Talent And Fame
- 1st Studio Siberian Mouse
Table of Contents
- Why Secure IoT Connections to AWS VPC Matter So Much
- Key AWS Services for Secure IoT Connectivity
- Designing Your Secure Connection Architecture
- Best Practices for a Bulletproof Setup
- Frequently Asked Questions
- Conclusion
Why Secure IoT Connections to AWS VPC Matter So Much
When you're dealing with remote IoT devices, they're often out there in the real world, far from your main office. These devices might be collecting all sorts of information, some of it quite sensitive. So, ensuring a secure connection back to your central cloud environment, your AWS VPC, is not just a nice-to-have; it's a must. It's a bit like making sure your online banking connection is secure; you just expect it, don't you?
The Risks of Unprotected Connections
Without strong security, your IoT devices and the data they send are, well, pretty exposed. Think about it: an attacker could potentially listen in on your data as it travels, which could mean a serious privacy breach. They might even try to send fake commands to your devices, causing them to do things they shouldn't, like turning off critical equipment or giving incorrect readings. That's a very real concern for many businesses, actually.
There's also the risk of someone gaining unauthorized access to your broader AWS environment through a vulnerable IoT device. If a device isn't properly secured, it could become a weak link, allowing an intruder to sneak into your private network. This is why making sure you can `securely connect remoteiot vpc aws` is so important. It's about protecting your entire digital footprint, in a way.
Keeping Your Data Safe
A secure connection means your data is encrypted, meaning it's scrambled up so only the intended recipient can read it. It also means that only authorized devices can talk to your AWS VPC, and only authorized services within your VPC can talk back to those devices. This creates a kind of digital fortress around your IoT operations, keeping your information private and your systems running as they should. It's all about building trust in your data flow, too.
Key AWS Services for Secure IoT Connectivity
AWS offers a range of services that work together to help you `securely connect remoteiot vpc aws`. Understanding how these pieces fit is a big part of building a strong and reliable system. It's like having the right tools for a job, you know?
AWS IoT Core: The Central Hub
AWS IoT Core is, basically, the heart of your IoT setup in AWS. It allows billions of devices to connect and interact with AWS services without you having to manage servers. It handles device authentication, authorization, and message routing. What's really neat is that it uses strong security protocols like TLS (Transport Layer Security), which helps ensure that data is encrypted as it travels. This is similar to how your browser tries to connect securely to websites, avoiding those "cannot connect securely to this page" messages due to outdated security.
IoT Core also lets you set up policies that define what each device is allowed to do. So, if a sensor should only send temperature data and nothing else, you can make sure of that. It's all about giving just the right amount of access, and no more, which is a very good practice.
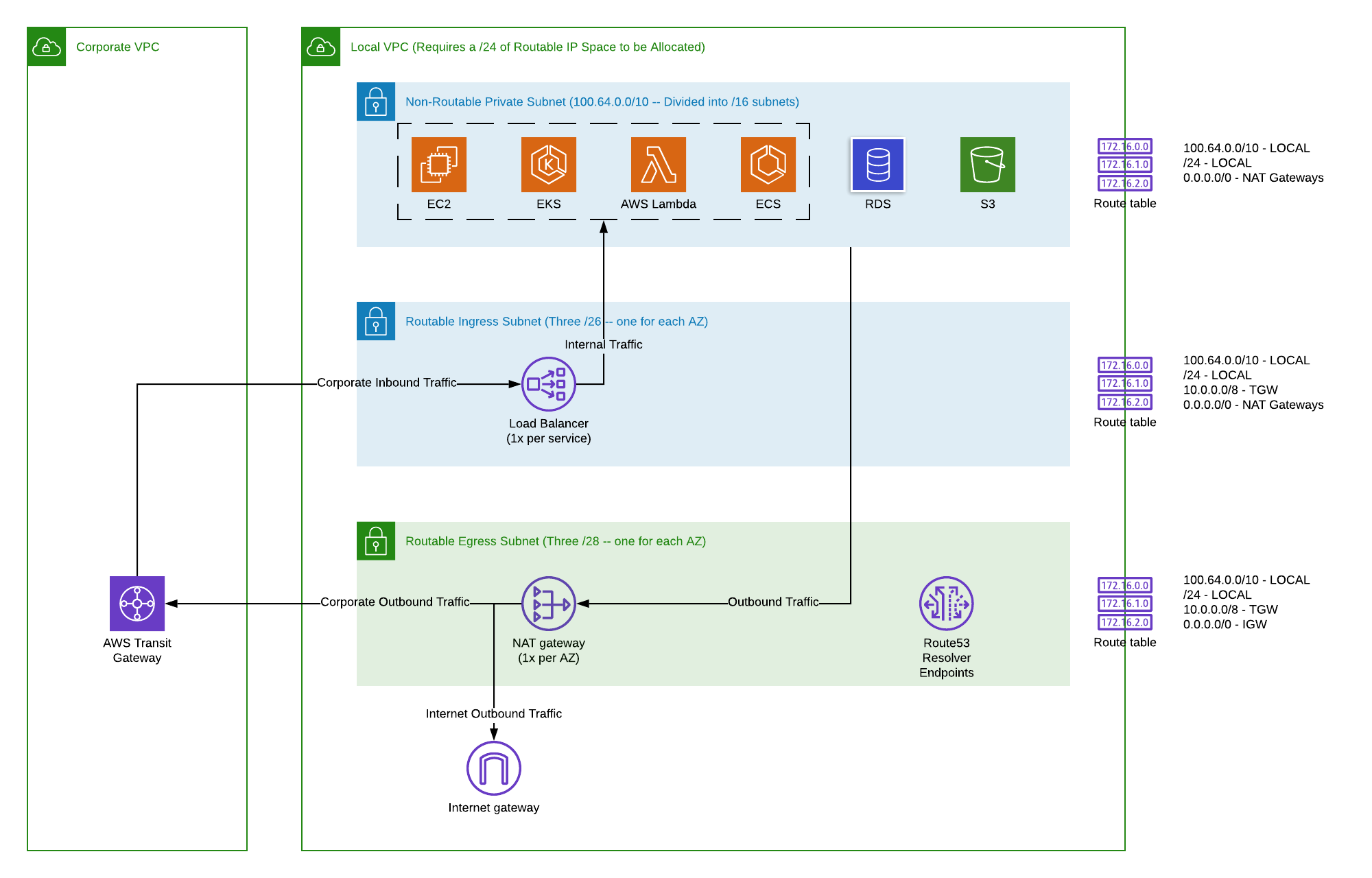
Virtual Private Cloud (VPC): Your Private Network Space
Your AWS VPC is like your own isolated, private network within the AWS cloud. You get to define its IP address range, set up subnets, and configure network gateways. This isolation is a huge security benefit because it means your IoT applications and data processing services aren't exposed to the public internet unless you specifically allow it. It's your own little corner of the cloud, basically.
When you `securely connect remoteiot vpc aws`, you're often trying to get your device data *into* this private space for processing and storage, keeping it away from prying eyes. It's a fundamental building block for any secure cloud setup, really.
AWS PrivateLink: Direct, Secure Paths
AWS PrivateLink is a pretty clever service that lets you connect your VPC to AWS services (like IoT Core) or other VPCs without sending traffic over the public internet. Instead, it creates a private endpoint within your VPC. This means your IoT devices, once they've connected to IoT Core, can then send their data directly and privately into your VPC through this endpoint. It's a bit like having a secret tunnel, if you will, that only your data can use. This significantly reduces the attack surface and helps you meet compliance requirements, too.
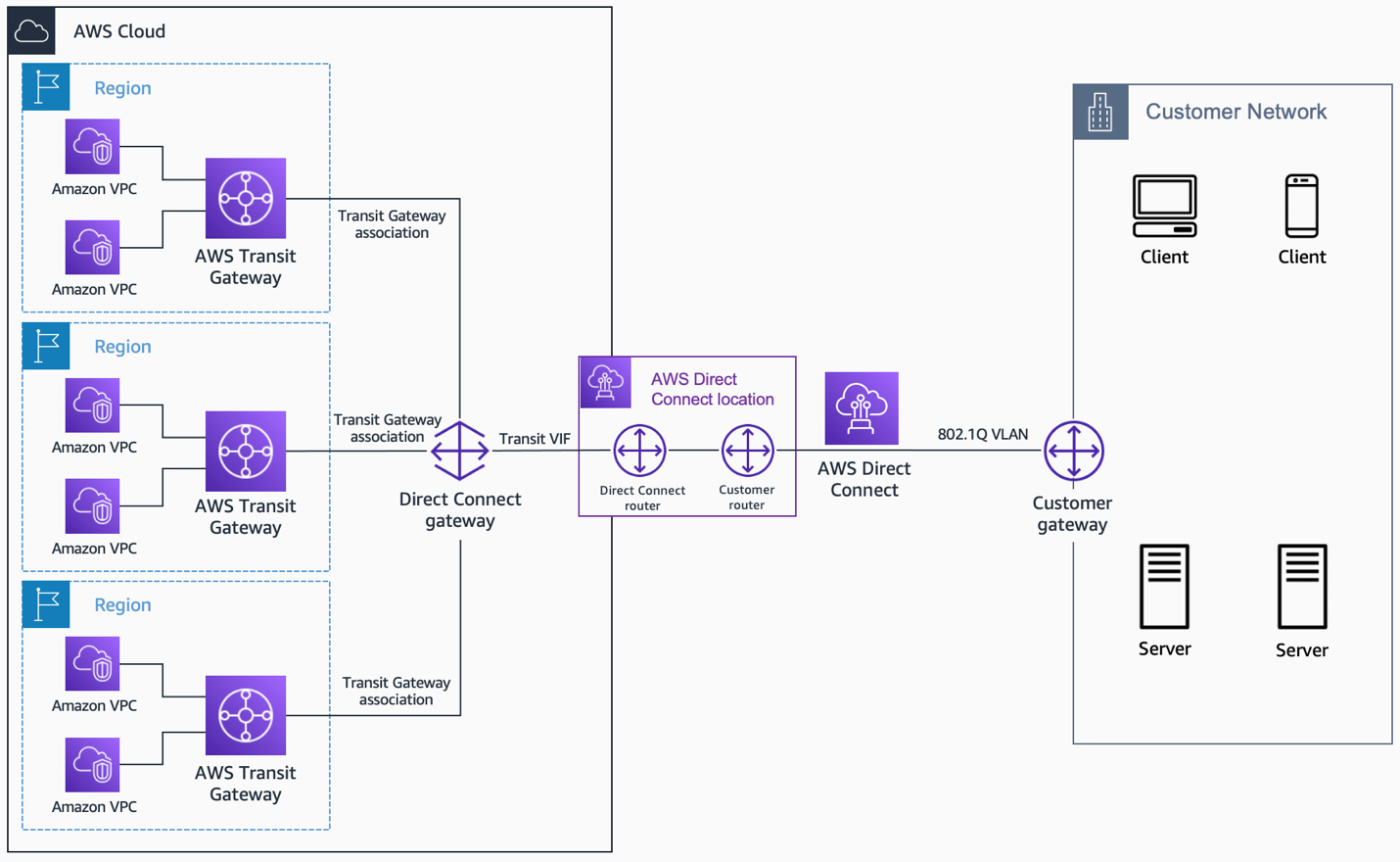
AWS Client VPN and Site-to-Site VPN: Building Secure Tunnels
For some remote IoT scenarios, especially where you have a gateway device or a small local network of devices, using a VPN might be a good fit. AWS Client VPN allows individual devices or users to connect securely to your VPC. Site-to-Site VPN, on the other hand, connects your on-premises network directly to your VPC, creating a secure tunnel. This is useful if your IoT devices are behind a firewall in a factory or office and you want to route all their traffic through a secure gateway. It's another way to ensure that critical data, like the financial documents mentioned in your text, travels safely, just in a different context.
AWS IoT Greengrass: Extending AWS to the Edge
AWS IoT Greengrass brings AWS capabilities right to your edge devices. This means you can run AWS Lambda functions, machine learning models, and other AWS services directly on your IoT devices or local gateways. Greengrass devices can connect to AWS IoT Core and other AWS services using secure, encrypted connections. It's a way to process data closer to where it's generated, reducing latency and sometimes the amount of data you need to send back to the cloud. This can also help with security by processing sensitive data locally before sending only aggregated or less sensitive information to the cloud. It's pretty versatile, you know.
Designing Your Secure Connection Architecture
Putting these services together to `securely connect remoteiot vpc aws` requires some thought. It's not just about turning things on; it's about designing a system that works for your specific needs and keeps everything safe. You want to build something reliable, that's what.
Authentication and Authorization: Knowing Who's Who
Every single IoT device that tries to connect to your AWS environment needs to prove its identity (authentication) and then be told what it's allowed to do (authorization). AWS IoT Core uses X.509 certificates and AWS IAM policies for this. Each device gets a unique certificate, and you attach policies to these certificates that define permissions. This is a bit like giving each client a unique, secure link for uploading confidential documents, ensuring only they can access it. It's a very strong way to manage access, in some respects.
Make sure your devices are provisioned with unique credentials and that these credentials are never shared. Rotating certificates regularly is also a smart move, just like changing your passwords now and then. It keeps things fresh and harder to compromise, actually.
Data Encryption: Scrambling the Information
From the moment data leaves your IoT device until it's processed and stored in your AWS VPC, it should be encrypted. AWS IoT Core handles encryption in transit using TLS. For data at rest, you should use services like Amazon S3 with server-side encryption or Amazon DynamoDB with encryption at rest. This ensures that even if someone manages to get their hands on your stored data, they won't be able to read it without the right keys. It's a bit like putting your sensitive files in a locked safe, you know?
Network Isolation: Keeping Things Separate
Within your AWS VPC, use subnets, security groups, and network access control lists (ACLs) to create layers of isolation. Your IoT data processing applications should ideally live in private subnets, with no direct public internet access. Use security groups to act as virtual firewalls, controlling traffic in and out of your instances and services. This helps contain any potential issues and prevents unauthorized lateral movement within your network. It's about building walls within your fortress, basically.
Monitoring and Logging: Watching Over Your System
You can't secure what you can't see. Use AWS CloudWatch and AWS CloudTrail to monitor your IoT connections and activities. CloudWatch lets you set up alarms for unusual behavior, like a device trying to connect from an unexpected location or sending an unusually large amount of data. CloudTrail logs all API calls made in your AWS account, giving you an audit trail of who did what, and when. This is similar to how you'd want to confirm that a secure email was indeed sent securely; you need a way to verify the process. It's very important to keep an eye on things, you know.
Best Practices for a Bulletproof Setup
Beyond the services themselves, there are some general rules of thumb that will help you `securely connect remoteiot vpc aws` in the best way possible. These are tried-and-true methods for good security.
Least Privilege: Only What's Needed
This is a fundamental security principle. Grant your IoT devices and the services they interact with only the minimum permissions they need to do their job, and no more. If a device only needs to publish data to a specific topic, don't give it permission to subscribe to all topics or update device shadows. This limits the damage if a device is ever compromised. It's like giving someone a key only to the room they need to enter, not the whole building, basically.
Regular Security Audits: Checking for Weak Spots
Technology changes, and so do threats. Regularly review your IoT security configuration, device firmware, and network settings. Look for outdated security protocols, like those that might cause a "can't connect securely to this page" error. Penetration testing can also help uncover vulnerabilities before malicious actors do. It's about being proactive, you know, staying ahead of the curve.
Device Lifecycle Management: From Start to Finish
Think about the entire life of your IoT devices, from when they're first provisioned to when they're retired. How are new devices securely onboarded? How are their credentials managed throughout their operational life? What happens when a device needs to be decommissioned? Ensuring secure practices at each stage, including securely erasing data from devices before recycling them (similar to securely erasing a hard disk), is crucial. It's a complete picture, really.
Secure Software Updates: Keeping Devices Current
IoT devices often run embedded software that needs updates. Make sure you have a secure over-the-air (OTA) update mechanism in place. Updates should be signed and verified by the device to prevent malicious firmware from being installed. An outdated device can be a serious security risk, just like an operating system with unpatched vulnerabilities. Keeping things current is pretty important, honestly.
Frequently Asked Questions
Here are some common questions people often ask about connecting IoT devices securely to AWS:
How do I connect IoT devices to a private VPC in AWS?
You typically use AWS IoT Core as the initial connection point for your devices. Then, you can leverage services like AWS PrivateLink to create a private, direct connection from IoT Core into your specific VPC. Alternatively, for certain setups, you might use AWS Client VPN or Site-to-Site VPN to create secure tunnels into your VPC for device traffic. It depends on your setup, you know.
What are the security options for AWS IoT Core?
AWS IoT Core offers robust security features. These include strong device authentication using X.509 certificates, authorization through fine-grained AWS IAM policies, and encryption of data in transit using TLS. It also integrates with AWS services like CloudWatch and CloudTrail for monitoring and logging, which is pretty handy.
Can I use VPN for IoT device connections to AWS?
Yes, you certainly can. For individual devices or groups of devices behind a gateway, AWS Client VPN can establish secure connections to your VPC. For connecting an entire on-premises network where your IoT devices reside, an AWS Site-to-Site VPN can create a secure tunnel into your VPC. This is often used when devices are not directly exposed to the internet, you know.
Conclusion
Making sure you `securely connect remoteiot vpc aws` is a foundational step for any successful IoT deployment. It's about protecting your data, your devices, and your entire cloud infrastructure from potential threats. By using AWS services like IoT Core, VPC, PrivateLink, and others, and by following smart security practices, you can build a robust and private system that you can trust. This approach helps ensure that your sensitive IoT data is handled with the same care you'd expect for any confidential information, like the financial documents you mentioned earlier. It's all about peace of mind, really. Learn more about secure cloud connectivity on our site, and link to this page for more IoT security tips.
- Selena Quintanilla Outfits A Timeless Fashion Legacy
- Snow Bunny Girl Meaning
- Scream Vii Everything You Need To Know About The Upcoming Horror Sequel
- 1st Studio Siberian Mouse
- Was The Shah Of Iran A Good Leader
AWS VPC Subnets, Routing Tables And Internet Access Using, 56% OFF

AWS VPC Tutorial - Part I Introduction - StudyTrails
Securely Connect Remote IoT VPC AWS Not Working Windows: Comprehensive