Access IoT Device SSH Example: Your Guide To Secure Remote Control
Getting into your IoT devices remotely is a pretty big deal, especially when you need to check things out or make changes. This is where something called SSH, or Secure Shell, comes into play. It's a way to securely get "access" to your tiny computers, like those in your smart home gadgets or industrial sensors. You know, the word "access" itself has quite a few meanings; some folks might think of it as a Microsoft Office program for managing databases, like what's talked about in some older texts. But here, we're talking about something entirely different: gaining control over your connected hardware.
For many folks, the idea of talking directly to their smart thermostat or a remote sensor seems a bit like magic, or maybe even a little scary. But honestly, with SSH, it's really not that hard to gain that kind of direct control. It gives you a command line, which is basically a text-based way to tell your device what to do, from anywhere. It's like having a little window right into your device's brain, so to speak, allowing you to give it instructions or see what it's up to.
This article will walk you through what SSH is, why it's so useful for IoT, and then show you a clear, step-by-step example of how you can use it. We'll also touch on some important security tips, because keeping your devices safe is, you know, very important. It’s pretty crucial to understand how to keep things locked down, too, especially with so many devices online these days. So, let's get started on making your IoT experience a bit more hands-on and secure.
- %D9%83%D9%85 %D8%A7%D9%84%D9%85%D8%B3%D8%A7%D9%81%D8%A9 %D8%A8%D9%8A%D9%86 %D8%A7%D9%8A%D8%B1%D8%A7%D9%86 %D9%88%D8%A7%D8%B3%D8%B1%D8%A7%D8%A6%D9%8A%D9%84
- Who Are Zoe Perrys Parents Unveiling The Family Background Of The Talented Actress
- Pawgedcom
- Iranian Sexism
- Aishah Sofey Content
Table of Contents
- What is SSH and Why is it Great for IoT?
- Secure Communication
- Remote Management
- Troubleshooting Made Simple
- Preparing Your IoT Device for SSH Access
- Enabling SSH
- Finding Your Device's IP Address
- A Step-by-Step SSH Example: Connecting to Your IoT Gadget
- What You'll Need
- The SSH Command
- First Connection and Fingerprint Verification
- Entering Commands
- Keeping Your IoT SSH Connection Safe and Sound
- Strong Passwords or Key-Based Authentication
- Changing Default Ports
- Disabling Root Login
- Keeping Software Updated
- Common Issues and Quick Fixes
- Frequently Asked Questions About IoT SSH Access
What is SSH and Why is it Great for IoT?
SSH, which stands for Secure Shell, is a network protocol that gives you a secure way to operate network services over an unsecured network. It's a bit like creating a private, protected tunnel through the internet directly to your device. This secure connection is pretty vital, especially when you're dealing with sensitive data or just want to make sure no one else is messing with your gadgets. It’s designed to be a safe path, so to speak, for your commands and data to travel.
Secure Communication
One of the biggest reasons to use SSH for your IoT devices is the security it offers. When you use SSH, all the information exchanged between your computer and the IoT device is encrypted. This means that even if someone were to intercept your data, they wouldn't be able to make sense of it. It's like sending a secret message in a code that only you and your device know how to crack. This protection is, you know, really important for keeping your private stuff private, especially in today's digital world where security threats are pretty common.
This encryption applies to everything, from the commands you send to the responses you get back. So, whether you're telling your device to turn off a light or checking its system logs, you can be pretty confident that no one is eavesdropping or tampering with the information. It’s a very robust way to communicate, arguably the best standard method for this kind of remote work. As a matter of fact, many professionals rely on it daily for mission-critical systems.
- Aishah Sofey Erome
- Exploring Malachi Bartons Relationships The Young Stars Personal Connections
- Bomb Iran Vince Vance
- Eliza Leaks
- What Was Lol Superman
Remote Management
Imagine you have a sensor out in the field, maybe monitoring temperature in a remote location, or a smart sprinkler system in your garden that needs a tweak. Going out to physically connect a keyboard and screen to each device every time you need to do something would be, well, a real pain. SSH lets you manage these devices from pretty much anywhere you have an internet connection. You can send commands, install updates, or even restart the device, all without leaving your comfy chair. This capability is very convenient, and it saves a lot of time and effort.
This remote management capability is especially helpful for devices that are difficult to reach or are deployed in large numbers. Think about a smart city project with hundreds of streetlights, each with an IoT controller. SSH makes it possible to manage all of them efficiently from a central location. It really streamlines operations, making maintenance and updates a lot simpler, which is a significant advantage for any large-scale deployment. Basically, it gives you the freedom to control your tech without being physically present.
Troubleshooting Made Simple
Sometimes, your IoT device might act up. Maybe it stops sending data, or a certain feature isn't working as it should. With SSH, you can log directly into the device and look at its system logs, check running processes, or even run diagnostic commands. It’s like being able to open up the hood of your car and poke around, even if the car is miles away. This direct access is incredibly valuable for figuring out what’s wrong and fixing it quickly, saving you a lot of headaches. You know, it's pretty much essential for effective problem-solving.
Without SSH, troubleshooting often means physically going to the device, perhaps connecting a monitor and keyboard, which can be time-consuming and difficult, especially if the device is in an awkward spot. SSH turns what could be a major expedition into a few quick commands from your computer. It makes life a lot easier for anyone managing IoT devices, allowing for quicker resolutions and less downtime. So, it's a very practical tool for keeping your systems running smoothly.
Preparing Your IoT Device for SSH Access
Before you can actually use SSH to connect to your IoT device, there are a couple of things you need to set up on the device itself. This usually involves enabling the SSH server software and figuring out its network address. These steps are pretty straightforward for most common IoT platforms, like Raspberry Pi or similar single-board computers. You know, it's just about getting things ready for the connection.
Enabling SSH
Most IoT operating systems, especially those based on Linux, come with an SSH server that you can enable. For a Raspberry Pi, for example, you can enable SSH through the `raspi-config` tool, or by simply placing an empty file named `ssh` (no extension) in the boot partition of the SD card before you even boot it up. This tells the system to start the SSH service when it powers on. It's a very common first step, and the exact method can vary a little depending on your specific device and its operating system. Make sure you check your device’s documentation for the precise steps, as this is pretty important.
Some devices might have SSH enabled by default, but it's often a good idea to check and perhaps disable it if you don't plan on using it immediately, just for security reasons. If you do enable it, you'll also want to make sure you set a strong password for the default user, or better yet, set up key-based authentication right away. This initial setup is, in some respects, the most critical part for a secure connection. You know, getting this right from the start saves a lot of trouble later on.
Finding Your Device's IP Address
To connect to your IoT device using SSH, you need to know its IP address on your local network. This is like its street address on the internet. You can usually find this in a few ways. If your device has a display, you might be able to see it in the system settings. Otherwise, you can often log into your router's administration page and look at the list of connected devices. Tools like `nmap` or even simple network scanners on your computer can also help discover devices on your network. It's a very necessary piece of information for making that connection happen.
Sometimes, devices are configured to use a static IP address, which means it won't change. More often, they get a dynamic IP address from your router, which can change over time. For reliable SSH access, especially if you're planning on connecting often, it might be a good idea to configure your router to assign a static IP address to your IoT device based on its MAC address. This way, you'll always know where to find it. This step, you know, makes things a lot more convenient in the long run.
A Step-by-Step SSH Example: Connecting to Your IoT Gadget
Alright, let's get to the practical part. Here’s a basic example of how you would use the SSH command to connect to an IoT device, like a Raspberry Pi, from your computer. This assumes you've already enabled SSH on your device and know its IP address. This is, basically, the core of what you came here to learn, so pay close attention. It's pretty straightforward once you get the hang of it.
What You'll Need
- Your IoT device (e.g., Raspberry Pi) with SSH enabled and connected to your network.
- The IP address of your IoT device (e.g., 192.168.1.105).
- A computer with an SSH client installed. Most Linux and macOS systems have it built-in. For Windows, you can use PowerShell, Windows Terminal, or a tool like PuTTY. Very common tools, so you probably already have something that works.
- The username and password for a user account on your IoT device (e.g., 'pi' and 'raspberry' for a default Raspberry Pi setup).
The SSH Command
Open a terminal or command prompt on your computer. The basic command structure is `ssh [username]@[IP address]`. So, if your username on the Raspberry Pi is 'pi' and its IP address is 192.168.1.105, you would type: `ssh pi@192.168.1.105` and then press Enter. It's a very simple command, really, but it opens up a whole world of possibilities. You know, it’s the gateway.
You might also specify a different port if your SSH server isn't running on the default port 22. In that case, you'd add `-p [port_number]` to the command. For example: `ssh pi@192.168.1.105 -p 2222`. This is a pretty common security measure, actually, to move the SSH service to a less obvious port. It’s just a little extra step for better protection, which is always a good idea.
First Connection and Fingerprint Verification
The very first time you connect to a new device, your SSH client will show you a message about the host's authenticity and ask if you want to continue. It will display something called an "ECDSA key fingerprint" or similar. This fingerprint is a unique identifier for the device you're connecting to. You should compare this fingerprint with the one stored or displayed on your IoT device, if possible, to make sure you're connecting to the right one and not some impostor. This step is, you know, very important for security.
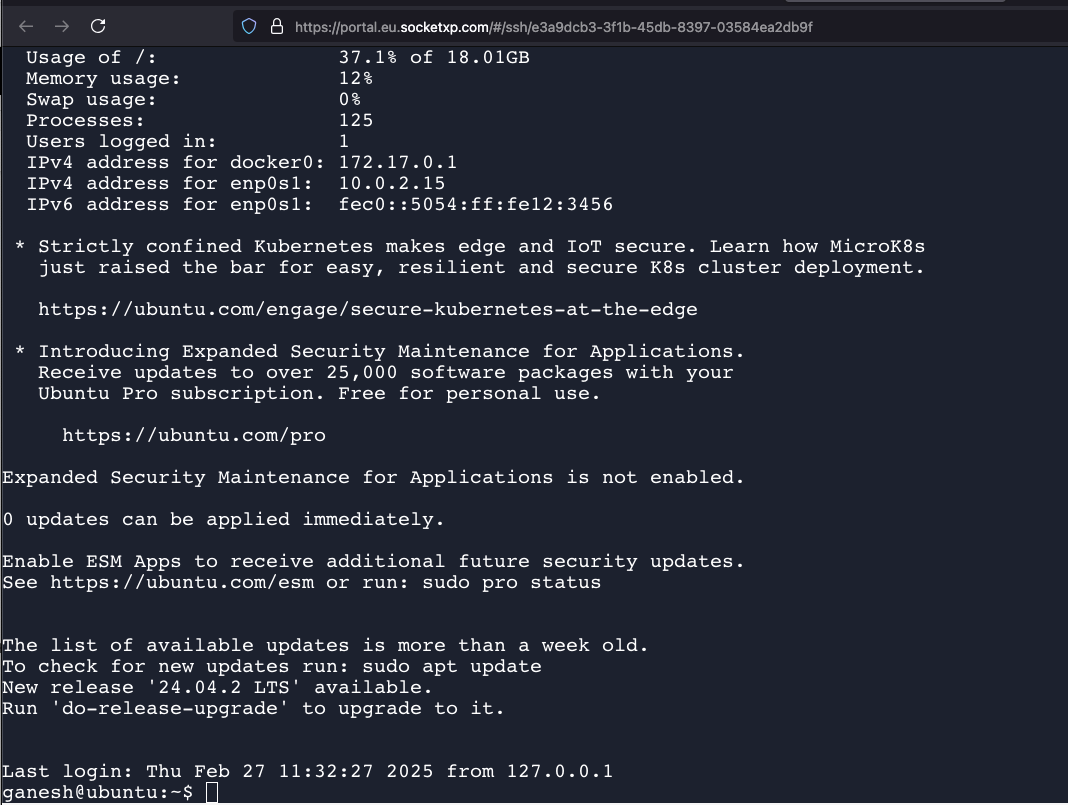
If the fingerprints match, type `yes` and press Enter. The client will then add the device's fingerprint to your computer's `known_hosts` file. After this, you'll be prompted to enter the password for the user account on your IoT device. Type the password (it won't show up as you type, which is normal for security) and press Enter. If everything is correct, you'll see a command prompt that looks like it's coming directly from your IoT device. You’re in! It's a pretty satisfying moment, to be honest.
Entering Commands
Once you're connected, you can type Linux commands just as if you were sitting right in front of the device. For example, you can type `ls -l` to list the files in the current directory, or `sudo apt update` to update the software packages on your Raspberry Pi. When you're finished, simply type `exit` and press Enter to close the SSH connection. It's very intuitive once you get going, and you can do pretty much anything you'd do locally. This capability is, you know, quite powerful for remote operations.
You can also transfer files using tools like `scp` (Secure Copy Protocol) or `sftp` (SSH File Transfer Protocol), which also use SSH for secure communication. These are separate commands but rely on the same underlying SSH connection. So, if you need to upload a new script or download some sensor data, these tools make it pretty easy and safe. It's just another way SSH extends its usefulness for managing your devices. Learn more about IoT basics on our site, and link to this page secure device setup for more helpful information.
Keeping Your IoT SSH Connection Safe and Sound
While SSH provides a secure channel, how you configure and use it on your IoT devices matters a lot for overall security. Neglecting basic security practices can leave your devices vulnerable. It's like having a very strong lock on your front door but leaving a spare key under the doormat. So, you know, it’s pretty important to follow some best practices to keep things secure.
Strong Passwords or Key-Based Authentication
The simplest and most important step is to use strong, unique passwords for your device accounts. Avoid default passwords like 'raspberry' for a Raspberry Pi. Even better, set up SSH key-based authentication. This uses a pair of cryptographic keys (a public key on the device and a private key on your computer) instead of passwords. It’s significantly more secure and convenient, as you don't have to type a password every time. You can learn more about this on the official OpenSSH website. It's a very recommended approach for serious security, honestly.
With key-based authentication, your private key never leaves your computer, and the public key on the device can't be used to generate the private key. This makes it extremely difficult for attackers to gain access, even if they manage to steal the public key. It's a bit like having a unique digital signature that only you possess, allowing you to prove your identity to the device. This method is, arguably, the gold standard for secure SSH access, and it’s something you really should consider implementing.
Changing Default Ports
By default, SSH servers listen on port 22. Attackers often scan the internet for devices listening on this port, looking for easy targets. Changing your SSH server to listen on a non-standard port (e.g., 2222, 22222, or any unused port above 1024) makes your device less visible to these automated scans. It's not a foolproof security measure on its own, but it adds an extra layer of obscurity that can deter opportunistic attacks. This simple change is, you know, a pretty good idea for basic protection.
To do this, you'll need to edit the `sshd_config` file on your IoT device (usually located in `/etc/ssh/`). Find the line `Port 22`, change `22` to your desired port number, save the file, and then restart the SSH service. Remember that when you connect, you'll need to specify the new port using the `-p` option in your SSH command. This small adjustment can significantly reduce the amount of unwanted attention your device receives from the internet, which is very helpful.
Disabling Root Login
The 'root' user is the superuser on Linux systems, with full administrative privileges. Allowing direct SSH login as 'root' is generally discouraged because if an attacker gains access to the 'root' account, they have complete control over your device. Instead, log in as a regular user and then use `sudo` (Superuser Do) to execute commands that require elevated privileges. This means an attacker would need to compromise two sets of credentials to get full control. It's a very important security principle, honestly, to limit direct root access.
You can disable root login by editing the `sshd_config` file and setting `PermitRootLogin no`. After saving and restarting the SSH service, direct root logins will be prevented. This practice, you know, adds a significant barrier for potential intruders and is a widely accepted security recommendation for any Linux-based system, including your IoT devices. It makes your setup a lot more resilient against attacks.
Keeping Software Updated
Software vulnerabilities are discovered regularly. Keeping your IoT device's operating system and all installed software, including the SSH server, up to date is crucial. Updates often include security patches that fix known weaknesses. Regularly running commands like `sudo apt update` and `sudo apt upgrade` (for Debian-based systems like Raspberry Pi OS) will help keep your device protected against the latest threats. This is, basically, an ongoing task for good security hygiene. It's pretty essential for long-term safety.
Automating updates can be a good idea for devices that are difficult to access physically, but be careful with automatic updates on critical systems, as sometimes updates can introduce new issues. For IoT devices, a regular manual check or a carefully managed automated update process is typically recommended. Staying current with patches is, you know, a very effective way to guard against newly discovered security holes, keeping your devices more secure over time.
Common Issues and Quick Fixes
Even with careful setup, you might run into a few bumps when trying to access your IoT device via SSH. It happens, you know, with technology. Here are some common problems and what you can usually do about them.
If you get a "Connection refused" error, it often means the SSH server isn't running on your device, or a firewall is blocking the connection. Double-check that SSH is enabled on your device and that your network's firewall or router isn't blocking port 22 (or whatever custom port you're using). Sometimes, a simple restart of the device or the SSH service on the device can fix this. It's a very common first troubleshooting step, to be honest.
A "Permission denied" error usually points to incorrect username or password. Make sure you're using the correct credentials for a user account that has SSH access. If you're using SSH keys, verify that your private key is correctly loaded and that the public key is on the device in the right place (usually `~/.ssh/authorized_keys`). This error is, arguably, one of the most frequent ones people encounter, and it’s usually an easy fix once you check your details.
If the connection just hangs, or you get a "Connection timed out" message, it often means your computer can't reach the IoT device at all. This could be due to an incorrect IP address, the device being offline, or a network issue. Ping the device's IP address from your computer to see if it's reachable. If not, check the device's network connection and its IP address again. It’s pretty much a network problem at that point, so you know, check your cables and Wi-Fi.
Finally, if you see a warning about a "Host key verification failed," it means the fingerprint of the device you're trying to connect to has changed, or it doesn't match what your computer expects. This can happen if you've reinstalled the OS on your IoT device, or if its IP address was reassigned to a different device. It can also, very rarely, indicate a malicious "man-in-the-middle" attack. You'll need to remove the old entry from your `known_hosts` file (the SSH client usually tells you which line to remove) and then try connecting again. It's a pretty important warning, so don't just ignore it.
Frequently Asked Questions About IoT SSH Access
What is SSH and why use it for IoT?
SSH, or Secure Shell, is a network protocol that lets you securely operate network services over an unsecured network. You use it for IoT devices to gain secure, remote command-line access. This allows you to manage, configure, and troubleshoot your devices from anywhere, without needing to be physically present. It encrypts all communications, making it much safer than older, unencrypted methods. It's, you know, pretty much the standard for remote access.
How do I enable SSH on my IoT device?
The way you enable SSH varies a bit depending on your specific IoT device and its operating system. For many Linux-based devices like a Raspberry Pi, you can often enable it through a configuration tool (like `raspi-config`) or by placing a special file (like an empty `ssh` file) in the boot partition of its storage before starting it up. Always check your device's official documentation for the exact steps, as this is very important for proper setup.
What are the security risks of SSH on IoT devices?
The main security risks come from improper configuration or weak credentials. If you use weak, easily guessable passwords, or leave default settings unchanged (like allowing root login), your device could be vulnerable to unauthorized access. Attackers might try to brute-force passwords or exploit known vulnerabilities in outdated software. That's why using strong passwords or SSH keys, changing default ports, disabling root login, and keeping software updated are, you know, very important practices.

IoT SSH Remote Access - SocketXP Documentation

Remote Access IoT Device SSH: A Comprehensive Guide
How to Remote Access IoT SSH over the Internet