Securely Connect Remote IoT To Your VPC: Keeping Your Data Safe
Connecting devices from far away to your private cloud space is a big deal these days. You want to make sure everything stays safe and sound, especially with all the important information moving around. It is a bit like making sure your sensitive financial documents are uploaded securely, right? You just want that peace of mind, knowing your systems are protected from unwanted visitors or data problems.
Many businesses are finding that having devices out in the field, collecting all sorts of useful data, can really help them grow. But, how do you bring all that information back to your main system without putting it at risk? That is the real question, and it is something many people wonder about, just like how to confirm an email was sent securely, you know?
This article will walk you through how to securely connect remote IoT to your VPC. We will look at what makes these connections strong and how you can keep your data private and sound. It is all about building trust in your digital links, so your operations can run smoothly, and your information stays protected, like your customer files on SharePoint.
- Asianbunnyx Leaks
- Joe Pesci Health A Comprehensive Look At The Iconic Actors Wellbeing
- What Does The Term Eiffel Tower Mean
- 1st Studio Siberian Mouse
- What Was Lol Superman
Table of Contents
- Why Connecting Remote IoT to Your VPC Matters
- Understanding Your Connection Points
- Core Ways to Securely Connect Remote IoT to Your VPC
- Practical Steps for a Safer Connection
- Addressing Common Questions (FAQs)
- Looking Ahead: The Future of IoT Security
Why Connecting Remote IoT to Your VPC Matters
Think about all the tiny devices out there, gathering information for your business. Maybe they are sensors checking temperature in a warehouse, or perhaps cameras watching a distant site. All that information needs a safe way to get back to where it can be used, typically a virtual private cloud, or VPC. So, connecting these remote IoT devices to your VPC securely is really important, you know?
Without proper security, this data could fall into the wrong hands. It is a bit like leaving your financial documents in an unlocked cabinet. You would not want that, would you? Keeping those connections safe protects your business secrets and your customers' trust, which is pretty important, actually.
A good, secure connection means your systems run without a hitch. It helps avoid those frustrating "cannot connect" messages that can stop work cold. Plus, it makes sure your data is accurate and reliable, which is what you want for making good business choices.
- Denzel Washington Training Day
- Who Are Zoe Perrys Parents Unveiling The Family Background Of The Talented Actress
- Aishah Sofey Content
- Morgan Wallen Concert Length
- Ifsa Sotwe Turk
The Big Picture: What's at Stake?
When you connect devices that are far away to your main cloud system, a lot is on the line. First off, there is the privacy of your data. This could be anything from customer details to how your machines are running, so it really needs to be kept private, you see.
Then there is the chance of someone getting into your system without permission. If a bad actor gets in through a weak IoT device, they could mess with your operations or even steal information. That is a situation you definitely want to avoid, and it is something we all worry about, like when we cannot connect securely to a page, right?
Finally, there is the matter of staying within the rules. Many industries have strict guidelines about how data must be handled and protected. A secure connection helps you meet these rules, which keeps your business in good standing. It is pretty much a must-have these days, to be honest.
Common Worries for Businesses
Businesses often worry about a few key things when it comes to connecting remote IoT. One big concern is simply losing data or having it changed without permission. Imagine if a sensor reported incorrect readings because someone tampered with it; that could cause big problems, so, you want to prevent that.
Another worry is that a device might stop working because of a security issue. If a device gets infected, it could stop sending data or even spread bad things to other parts of your network. This is similar to a software update that keeps failing and trying to reinstall, causing a headache, you know?
And then there is the cost. Dealing with a security breach can be very expensive, not just in fixing the problem, but also in lost trust and reputation. Preventing these issues by securing your connections from the start saves money and stress in the long run. It is a pretty clear choice, more or less.
Understanding Your Connection Points
Before we get into how to secure things, it helps to know what we are talking about. We have remote devices, the Internet of Things, and your private cloud space. Getting a handle on each piece makes the whole picture clearer, and that is actually pretty helpful.
Knowing what each part does helps you see where the security needs to be strongest. It is a bit like understanding how your email works before you try to encrypt an attachment. You need to know the basics first, you know?
So, let us take a quick look at these parts. It will give us a good foundation for discussing how to keep everything safe and sound. We are just setting the stage, really.
What is IoT, Really?
IoT stands for the Internet of Things. These are everyday objects, or specialized sensors and machines, that have tiny computers inside them. They can connect to the internet and send or receive information. Think of smart thermostats, industrial sensors, or even smart streetlights, you know?
These devices often have very limited power and processing ability. This makes securing them a bit different from securing a regular computer. They might not be able to run heavy security software, for example. So, we have to think about that, pretty much.
Their main job is to collect data and send it somewhere, or sometimes to act on commands. They are the eyes and ears of your business out in the physical world. Getting that information back safely is the key, and that is what we are focusing on, literally.
VPC: Your Private Cloud Space
A VPC, or Virtual Private Cloud, is like having your own private section of a big public cloud. It is a place where you can put your servers, databases, and applications. It is isolated from other users of the cloud, which gives you a lot more control, you know?
Inside your VPC, you decide who can get in and out, and what can talk to what. This is where your IoT data usually ends up for storage and analysis. It is your main data hub, so to speak, and it is where you want to keep your valuable information, like your customer files, securely.
Setting up your VPC correctly is a big part of security. You are building the walls and gates for your digital property. So, understanding how to configure it is pretty important, actually.
The Remote Part
The "remote" part means these IoT devices are not sitting in your office or data center. They are out in the field, maybe in a factory, on a farm, or even inside someone's home. This distance creates unique challenges for connecting them safely, and it is something you have to plan for, you know?
They might be connecting over public internet lines, which are not always the safest. Or they might be in places where physical security is hard to maintain. This means the connection itself needs to be very strong, and that is a real consideration.
Because they are far away, it can also be harder to update them or fix problems. This is why getting the initial setup right is so important. You want a connection that is stable and secure from the start, pretty much, so you do not have to deal with constant issues.
Core Ways to Securely Connect Remote IoT to Your VPC
Now, let us get into the how-to. There are several main ways to make sure your remote IoT devices talk to your VPC safely. These methods work together to build a strong defense for your data, and it is pretty much a layered approach.
It is not just one thing; it is a combination of different techniques. Think of it like putting several locks on a door, not just one. Each adds another layer of protection, which is a good idea, you know?
We will look at secure tunnels, how devices prove who they are, keeping data secret, and controlling who can access what. These are the main building blocks for a safe connection, and they are something you really need to get right.
Secure Tunnels: VPNs and Direct Connect
One of the best ways to securely connect remote IoT to your VPC is by creating a secure tunnel. This makes a private path over the public internet. It is like having a secret, protected road for your data, so nobody else can see what is traveling on it, you know?
A common way to do this is with a Virtual Private Network, or VPN. Your IoT device or a gateway device near it can set up a VPN connection to your VPC. All the data then travels through this encrypted tunnel, which is pretty neat, actually.
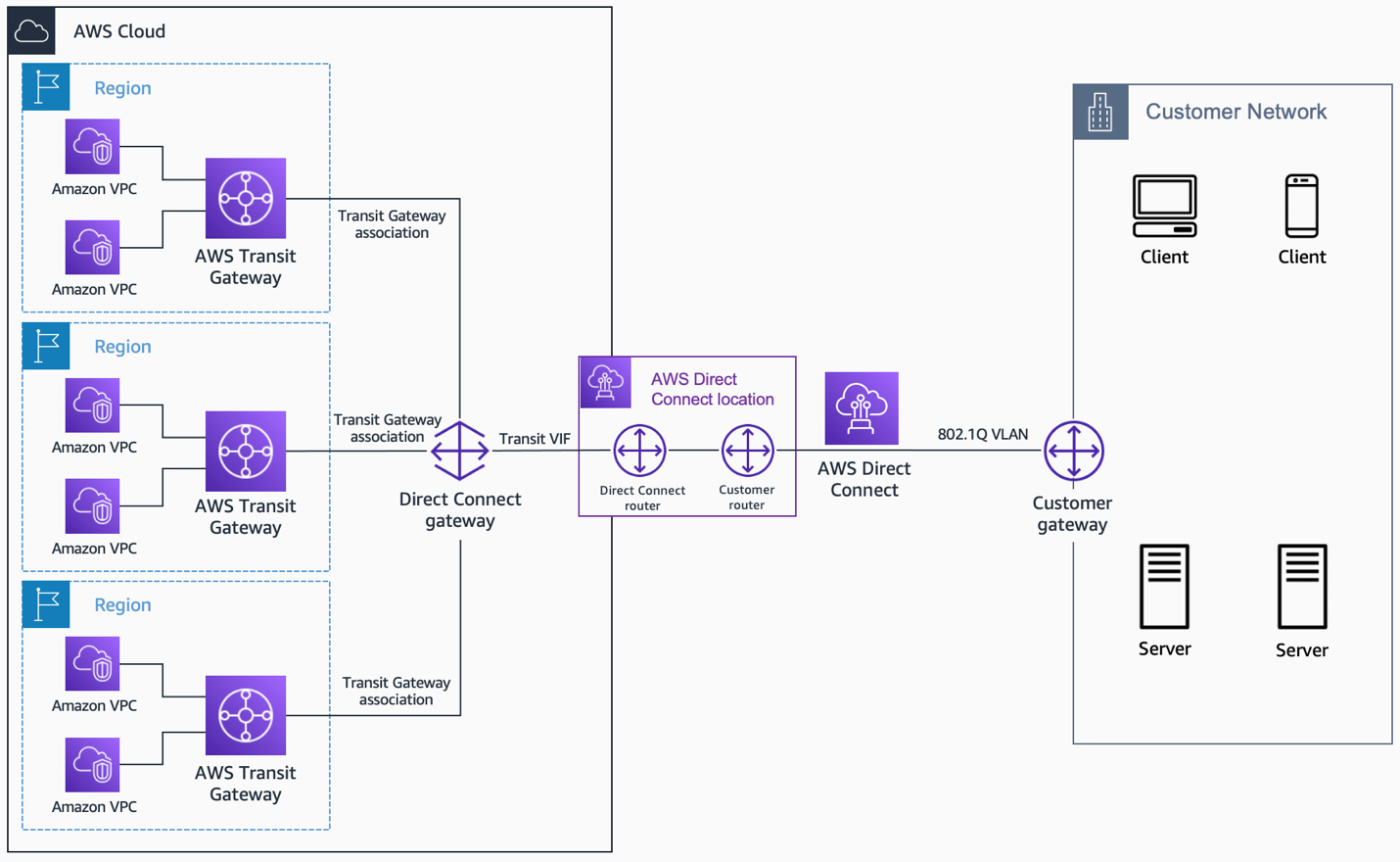
For even higher security and performance, especially if you have a lot of data, you might use something like a cloud provider's "Direct Connect" service. This creates a dedicated, private network line between your location and your VPC. It is even more secure than a VPN over the public internet, and it is something to consider for very sensitive data, you know?
Device Identity and Authentication
Just like you use a certificate and PIN to log in, your IoT devices need a way to prove who they are. This is called identity and authentication. You want to make sure only your real devices are connecting to your VPC, and not some imposter, you know?
Devices can use special digital certificates or unique keys to identify themselves. When a device tries to connect, your VPC checks this identity. If it matches, the device is allowed in; if not, it is kept out. It is a pretty simple idea, but very powerful, and it is something you definitely need to set up.
This helps stop fake devices from sending bad data or trying to get into your private cloud space. It is a crucial step in keeping your entire system safe. So, giving each device a clear identity is a very good move, honestly.
Data Encryption: In Transit and at Rest
Encryption means scrambling your data so only authorized people or systems can read it. You want to encrypt data both when it is moving (in transit) and when it is stored (at rest). This is like putting your confidential information into a locked box, and only you have the key, you know?
When data travels from your IoT device to your VPC, it should be encrypted. Protocols like TLS (Transport Layer Security) are used for this. If someone intercepts the data, it will just look like gibberish. This is very important, especially if the site uses outdated security, as your text points out.
Once the data arrives in your VPC and is stored, it should also be encrypted. Most cloud providers offer ways to automatically encrypt data stored in their services. This protects your data even if someone manages to get access to the storage itself. It is a pretty thorough approach, more or less.
Network Security Groups and Access Controls
Think of network security groups as digital bouncers for your VPC. They decide what kind of network traffic is allowed in and out of your servers and resources within the VPC. You can set rules to only allow connections from specific IP addresses or certain ports, which is a good idea, you know?
Access controls go a step further. They determine what specific actions a device or user can take once they are connected. For example, an IoT device might only be allowed to send data to a specific database, but not to change system settings. This is sometimes called "least privilege," meaning devices only get the permissions they absolutely need, and it is a very smart way to operate.
These controls help limit the damage if a device ever gets compromised. Even if a bad actor gets in, they cannot do much harm because their access is so limited. It is a pretty effective way to contain potential problems, honestly.
Monitoring Your Connections
Keeping an eye on your connections is like having a security guard watching your property. You want to know what is happening, who is connecting, and if anything looks out of the ordinary. This helps you spot problems quickly, which is pretty important, you know?
Cloud providers offer tools that let you see network traffic, connection attempts, and security alerts. You can set up alarms that tell you if something unusual happens, like too many failed login attempts from a device. This is similar to checking if a secure email was indeed sent securely; you want confirmation, you know?
Regularly reviewing these logs and alerts helps you understand your network's health. It also helps you catch potential security issues before they become big problems. Staying watchful is a key part of keeping things safe, more or less.
Practical Steps for a Safer Connection
Putting all these security ideas into practice can seem like a lot. But if you take it step by step, it is much more manageable. Here are some practical things you can do to securely connect remote IoT to your VPC, and it is something anyone can start with.
It is about being thoughtful in your approach, rather than just rushing into things. A little planning goes a long way in preventing future headaches, you know?
These steps will help you build a solid foundation for your IoT connections. They are pretty much common sense, but sometimes we just need a reminder, honestly.
Start with a Plan
Before you connect anything, sit down and draw out your network. Figure out what data each device will send, where it needs to go, and who needs to access it. A clear plan helps you identify potential weak spots early on, and that is a very good first step.
Think about the journey your data will take from the device to your VPC. What are the stops along the way? What kind of security does each stop need? This helps you pick the right tools and settings later, you know?
Also, consider what happens if something goes wrong. How will you fix it? Having a plan for problems is just as important as having a plan for the initial setup. It is like having a backup plan for your hard drives before recycling them, pretty much.
Pick the Right Tools
Your cloud provider, like AWS, Azure, or Google Cloud, offers many services designed for IoT and VPC security. Choose the ones that fit your needs best. For example, if you need secure file uploads, they have services for that, you know?
Look for services that handle device identity, secure messaging, and data storage with built-in encryption. Using tools designed for security often makes your job easier and more reliable. You do not have to build everything from scratch, which is pretty convenient, actually.
Do some research and see what others in your industry are using. Sometimes, the most popular tools are popular for a good reason. But always make sure they meet your specific security requirements, which is very important.
Test, Test, Test
Once you have everything set up, test your connections thoroughly. Try to break them, in a safe way, of course. See if you can send unauthorized data or if a device can connect when it should not. This helps you find any holes in your security before real problems happen, you know?
Simulate different scenarios, like a device losing connection and trying to reconnect. Does it re-establish securely? What happens if a device tries to send too much data? Testing helps you understand how your system behaves under various conditions, which is pretty useful.
Regular testing should be part of your ongoing security routine. Just like you might test a new software update, you should test your connections. It is a good way to stay on top of things, more or less.
Keep Things Updated
Security is not a one-time setup; it is an ongoing effort. New threats appear all the time, so you need to keep your devices, software, and cloud configurations updated. This is a bit like keeping your Windows operating system updated to fix bugs and security issues, you know?
Make sure your IoT devices receive regular software updates. These updates often include fixes for security weaknesses. If a device cannot be updated, you might need to replace it or put extra security around it. That is a real consideration.
Also, stay informed about new security features or recommendations from your cloud provider. They are always improving their services, and taking advantage of new features can make your connections even safer. Staying current is a pretty smart move, honestly.
Addressing Common Questions (FAQs)
How do you secure IoT data?
You secure IoT data by encrypting it when it moves and when it is stored. You also make sure only authorized devices can send data, using things like digital certificates. It is about layers of protection, like putting your confidential information in a secure digital vault, you know?
What is the best way to connect remote devices to a cloud VPC?
The best way often involves using secure tunnels, like VPNs, or dedicated private connections, such as Direct Connect services. These create a private path for your data over the internet, keeping it away from prying eyes. It is pretty much like building a private road for your data, so it stays safe.
Why is VPC security important for IoT?
VPC security is important for IoT because your VPC is where your sensitive IoT data lives. Good VPC security means you control who gets in, what they can do, and how your data is protected from unauthorized access or changes. It is your private digital space, and you want to keep it safe, just like your OneDrive account for sensitive documents, you know?
Looking Ahead: The Future of IoT Security
The world of IoT is always changing, and so are the ways we keep it safe. We are seeing more focus on devices that can fix themselves or report problems without human help. This makes security even stronger, and it is something to watch for, you know?
There is also a lot of work being done on making security easier to set up. Companies want to securely connect remote IoT to their VPC without needing a team of experts for every single device. This means simpler tools and more automated ways to protect data, which is pretty exciting, actually.
Staying current with these new ideas will help you keep your IoT connections safe well into the future. It is an ongoing journey, but one that is very important for any business using remote devices. You can learn more about cloud security on our site, and check out this page for more IoT solutions.
This commitment to security helps build trust, which is really what it is all about. It ensures your operations run smoothly and your valuable information stays private, today and tomorrow. It is pretty much a smart investment, honestly.
- Aishah Sofey Boobs Leak
- As The World Caves In Song Meaning
- Aishah Sofey New Leaked
- Lagos Cerca De Mi
- Many Summers Later Gravity Falls
Securely Connect Remote IoT VPC AWS Not Working Windows: Comprehensive

Securely Connect Remote IoT VPC Raspberry Pi: The Ultimate Guide

How To Securely Connect RemoteIoT VPC Raspberry Pi On Windows